The Ultimate List of Open Source Static Code Analysis Security Tools Nov 13, 2014 by Sarah Vonnegut Doing security the right way demands an army – of developers, security teams, and the tools that each uses to help create and maintain secure code. Validation Ensure source code put in to escrow is valid and complete. Our validation service (also known as software testing) checks the source code before it is placed in to escrow. We test the source code provided by the software developer, reassuring software users that it is accessible and useable should they need it.
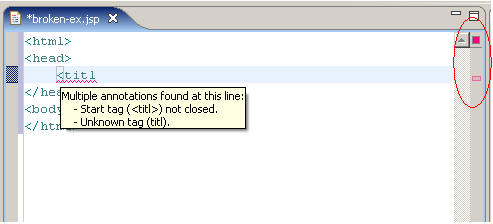
Regression: How to fix this
- The FDA has issued guidance for proper validation of medical device software in its General Principles of Software Validation. Skip to main content Products. All Products A - Z. Source code should be evaluated to verify its compliance with specified coding guidelines. Such guidelines should include coding.
- OpenCover is a free and open source code coverage tool for.NET 2 and above (Windows OSs only - no MONO), with support for 32 and 64 processes and covers both branch and sequence points. It uses the profiler API that is currently only available to.NET Frameworks running on the Windows platform.
- #2 and #3 are performed by the tool currently in openapi-validation-tools repo and by AutoRest linter. This project has.
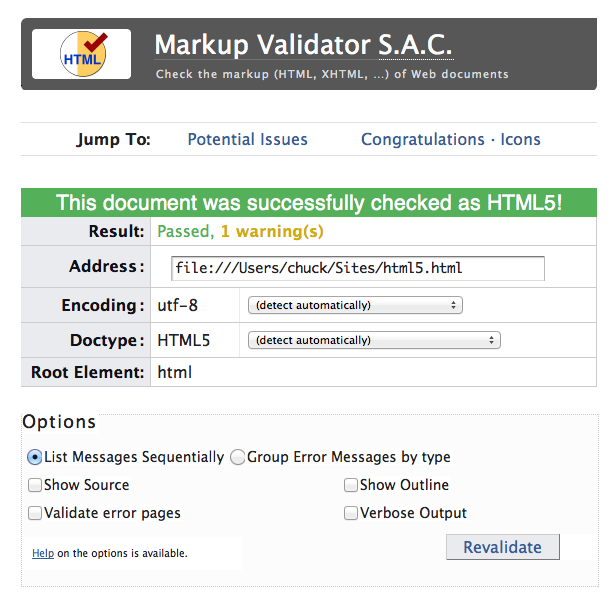
- By Sue Jenkins. Several fantastic free online website code validation tools are at your disposal. The W3C provides multiple tools that conform to and validate against the W3C’s latest recommended standards for CSS, HTML, XHTML, HTML5, and 508 accessibility.
Tools for validating OpenAPI (Swagger) files.
Requirements
- node.js version > 10.x
You can install the latest stable release of node.js from here. For a machine with a linux flavored OS, please follow the node.js installation instructions over here
How to install the tool
Command usage:
What does the tool do? What issues does the tool catch?
Model validation checks whether definitions for request parameters and responses, match an expected input/output payload of the service.
Examples of issues:
- required properties not sent in requests or responses;
- defined types not matching the value provided in the payload;
- constraints on properties not met; enumeration values that don’t match the value used by the service.
References: https://github.com/Azure/azure-rest-api-specs/issues/778 , https://github.com/Azure/azure-rest-api-specs/issues/755 , https://github.com/Azure/azure-rest-api-specs/issues/773
Model validation requires example payloads (request/response) of the service, so the data can be matched with the defined models. See x-ms-examples extension on how to specify the examples/payloads. Swagger “examples” is also supported and data included there is validated as well. To get the most benefit from this tool, make sure to have the simplest and most complex examples possible as part of x-ms-examples.
- Please take a look at the redis-cache swagger spec as an example for providing 'x-ms-examples' over here.
- The examples need to be provided in a separate file in the examples directory under the api-version directory
azure-rest-api-specs/arm-<yourService>/<api-version>/examples/<exampleName>.json. You can take a look over here for the structure of examples. - We require you to provide us a minimum (just required properties/parameters of the request/response) and a maximum (full blown) example. Feel free to provide more examples as deemed necessary.
- We have provided schemas for examples to be provided in the examples directory. It can be found over here. This will help you with intellisene and validation.
- If you are using vscode to edit your swaggers in the azure-rest-api-specs repo then everything should work out of the box as the schemas have been added in the
.vscode/settings.jsonfile over here. - If you are using Visual Studio then you can use the urls provided in the settings.json file and put them in the drop down list at the top of a json file when the file is opened in VS.
- If you are using vscode to edit your swaggers in the azure-rest-api-specs repo then everything should work out of the box as the schemas have been added in the
How does this tool fit with others
Swagger specs validation could be split in the following:
- Schema validation
- Semantic validation
- Model definition validation
- Swagger operations execution (against mocked data or live tests)
- Human-eye review to complement the above
In the context of “azure-rest-api-specs” repo:
- #1 is being performed on every PR as part of CI.
- #2 and #3 are performed by the tool currently in openapi-validation-tools repo and by AutoRest linter. We’re working towards integrating them into CI for “azure-rest-api-specs” repo.
- #4 is not available yet, though we’re starting to work on it.
- #5 will be done by the approvers of PRs in “azure-rest-api-specs”, as this won’t be automated.
Autorest plugin configuration
- Please don't edit this section unless you're re-configuring how oav plugs in to AutoRestAutoRest needs the below config to pick this up as a plug-in - see Autorest extensions.
Live Validation Mode
- A Live Validation mode has been added to OAV with the purpose of enabling validation of live traffic.
- Usage (here is a sample of a request-response pair):
Regression testing
Output of the OAV tool has been snapshotted and committed to the repo. The regression test may be run on a sample or all of https://github.com/azure/azure-rest-api-specs. If there are changes to the snapshots the build produces a git patch file as an artifact which may be used to update the snapshots.
Fast Regression (~10mins) is used for merge validation
Slow Regression (~1 hour) is run after merge and should be fixed if it fails
Fixing regression builds
- Go to the failed build
- Download the artifact patch file
- In the OAV directory run
git apply <path to patch file> - Commit the patched changes and create a pull request
- Validate that the changes look ok and don't represent a breaking change in OAV
- Merge the PR
This project has adopted the Microsoft Open Source Code of Conduct. For more information see the Code of Conduct FAQ or contact opencode@microsoft.com with any additional questions or comments.
List and comparison of the top best Static Code Analysis Tools:
Can we ever imagine sitting back and manually reading each line of codes to find flaws? To ease our work, several types of static analysis tools are available in the market which helps to analyze the code during the development and detect fatal defects early in the SDLC phase.
Such defects can be eliminated before the code is actually pushed for functional QA. A defect found later are always expensive to fix.
Read this to get an idea of what can help you the most based on your needs –
This is the list of top source code analysis tools for different languages.
What You Will Learn:
- Best Static Code Analysis Tools Comparison
Best Static Code Analysis Tools Comparison
Here is the list of the top 10 Static Code Analysis Tools for Java, C++, C# and Python:
- Raxis
- RIPS Technologies
- PVS-Studio
- Kiuwan
- Kritika
- Gamma
- DeepScan
- reshift
- CodeScene Behavioral Code Analysis
- Veracode
- Code Compare
- Fortify Static Code Analyzer
- Parasoft
Here is the detailed review of each.
#1) Raxis
Raxis does one better than automated tools that often discover false findings that waste time and effort.
Raxis scopes an amount of time that works best for your company’s code and assigns a security-focused former developer to analyze your code for both general security and business-logic vulnerabilities.
Raxis communicates throughout to be sure your input is used within the code review, and they provide a report that details each finding with screenshots and remediation advice. A high-level summary that can be provided to management and a debriefing call are also included.
=> Website link: Raxis Information Security
#2) RIPS Technologies
Custom Code Validation Tool
RIPS is the only code analysis solution that performs language-specific security analysis. It detects the most complex security vulnerabilities deeply nested within the source code that no other tools are able to find.
It supports major frameworks, SDLC integration, relevant industry standards and can be deployed as a self-hosted software or used as software-as-a-service. With its high accuracy and no false-positive noise, RIPS is the ideal choice for analyzing Java and PHP applications.
=> Website link: RIPS Technologies
#3) PVS-Studio
PVS-Studio is a tool for detecting bugs and security weaknesses in the source code of programs, written in C, C++, C# and Java. It works in Windows, Linux, and macOS environment.
It is possible to integrate it into Visual Studio, IntelliJ IDEA and other widespread IDE. The results of the analysis can be imported into SonarQube.
Enter the #top40 promo code in the message field on the download page to get the PVS-Studio license for a month instead of 7 weeks.
=> Website Link: Visit PVS-Studio
#4) Kiuwan
Kiuwan is a SAST and SCA platform with the largest technology coverage and integrations in the market.
With a DevSecOps approach, Kiuwan achieves outstanding benchmark scores (Owasp, NIST, CWE, etc) and offers a wealth of features that go beyond static analysis, catering to every stakeholder in the SDLC.
=> Website Link: Visit Kiuwan Code Security
#5) Kritika
Kritika.IO analyzes your code and provides useful information on your code style, code smells, complexity, duplications. It also analyzes open source dependencies licenses and looks for known vulnerabilities.
Kritika.IO integrates with GitHub, BitBucket and GitLab. It uses progressive pricing that depends solely on the amount of code analyzed. Analyzing open source projects is completely free and feature complete. Among unique languages, it supports Perl and Tcl.
=> Visit the official website: Kritika.IO
#6) Gamma
Gamma is an intelligent software analytics platform, developed by Acellere. It supports developers and teams in building higher quality software in less time, by speeding up code reviews.
It automatically prioritizes hotspots in the code and provides clear visualizations. With its multi-vector diagnostic technology, it analyses software from multiple lenses, including software design, and enables companies to manage and improve their software quality transparently.
=> Visit Website: Gamma
#7) DeepScan
DeepScan is an advanced static analysis tool engineered to support JavaScript, TypeScript, React, and Vue.js.
You can use DeepScan to find possible runtime errors and quality issues instead of coding conventions. Integrate with your GitHub repositories to get quality insight into your web project.
=> Visit Website: DeepScan.IO
#8) reshift
Reshift is a SaaS-based software platform that helps software development teams identify more vulnerabilities faster in their own code before deploying to production.
Reducing the cost and time of finding and fixing vulnerabilities, identifying the potential risk of data breaches, and helping software companies achieve compliance and regulatory requirements.
=> Visit Website: Reshift for more details
#9) CodeScene Behavioral Code Analysis
CodeScene prioritizes technical debt and code quality issues based on how the organization actually works with the code. Hence, CodeScene limits the results to information that is relevant, actionable and translates directly into business value.
CodeScene also goes beyond traditional tools by measuring the organization and people side of your system to detect coordination bottlenecks in the software architecture, off-boarding risks, and knowledge gaps.
Finally, CodeScene integrates into your CI/CD pipeline to act as an extra team member that predicts delivery risks and offers context-aware quality gates to supervise the health of your code.
=> Visit the official website: CodeScene
#10) Veracode
Veracode is a static analysis tool which is built on the SaaS model. This tool is mainly used to analyze the code from a security point of view.
This tool uses binary code/bytecode and hence ensures 100% test coverage. This tool proves to be a good choice if you want to write secure code.
=> Website Link: Veracode
#11) Fortify Static Code Analyzer
Fortify, a tool from HP which lets a developer build an error-free and secure code. This tool can be used by both development and security teams by working together to find and fix security-related issues. While scanning the code, it ranks the issues found and ensures the most critical ones are fixed first.
Website Link: Micro Focus Fortify Static Code Analyzer
#12) Parasoft
Parasoft, no doubt one of the best tools for Static Analysis Testing. This is slightly different when compared to other static analysis tools because of its ability to support various types of static analysis techniques like Pattern Based, Flow-Based, Third Party Analysis, and Metrics and Multivariate analysis. Another good thing about the tool is beside identifying defects it allows provides a feature which prevents defects.
Website Link: Parasoft
#13) Coverity
Coverity Scan is an open source cloud-based tool. It works for projects written using C, C++, Java C# or JavaScript. This tool provides a very detailed and clear description of the issues which helps in faster resolution. A good choice if you are looking for an open source tool.
Website Link: Coverity
#14) CAST
An automated tool which can be used to analyze more than 50+ languages works excellently regardless of the size of the project. In addition, it provides a Dashboard to users which help in measuring quality and productivity.
Website Link: CAST
#15) CodeSonar
A Static analysis tool by Grammatech not only lets a user find a programming error, but it also helps in finding out domain-related coding errors. It also allows customizing checkpoints and also built-in checks can be configured as per the requirement. Overall a great tool to detect security vulnerabilities and its ability to do a deep static analysis makes this stand out from the rest of the other static analysis tools available in the market.
Website Link: CodeSonar
#16) Understand
Just like its name, this tool lets user UNDERSTAND code by analyzing, measuring, visualizing and maintaining. This allows quick analysis of massive codes. This is one tool which is mainly used by aerospace and automakers industry. Supports major languages like C/C++, ADA, COBOL, FORTRAN, PASCAL, Python and other web languages.
Website Link: Understand
#17) Code Compare
Code Compare – is a file and folder comparison and merge tool. Over 70,000 users actively use Code Compare while resolving merge conflicts and deploying source code changes. Code Compare is a free compare tool designed to compare and merge differing files and folders. Code Compare integrates with all popular source control systems: TFS, SVN, Git, Mercurial, and Perforce. Code Compare is shipped both as a standalone file diff tool and a Visual Studio extension.
Key features:
- Text Comparison and Merging
- Semantic Source Code Comparison
- Folder Comparison
- Visual Studio Integration
- Version Control Integration and more
#18) Clang Static Analyzer
This is an open source tool which can be used to analyze a C, C++ code. It uses the clang library, hence forming a reusable component and can be used by multiple clients.
Website Link: Clang Static Analyzer
#19) CppDepend
A very easy to use the tool when compared to other static analysis tools. As the name suggests, this tool is used to analyze C/C++ codes. Supports different code quality metrics, provides facility to monitor trends, has an add-in to integrate with Visual Studio, allows writing custom queries and comes with a very good diagnostic facility.
Website Link: CppDepend
#20) Klocwork
Apart from finding semantics and syntax error, this tool also lets user detect vulnerabilities in the code. This tool is well integrated with many common IDE’s like Eclipse, Visual Studio, and Intellij IDEA. This can run in parallel to code creation, it does a line by line check and provides a feature for addressing the defects immediately.
Website Link: Klocwork
#21) Cppcheck
Another free static analysis tool for C/C++. The good thing about this tool is its integration with several other development tools like Eclipse, Jenkins, CLion, Visual Studio and many more. Its installer can be found at sourceforge.net.
Website Link: Cppcheck
#22) Helix QAC
Helix QAC is an excellent static analysis testing tool for C and C++ code from Perforce (formerly PRQA). The tool comes with a single installer and supports platforms like Windows 7, Linex Rhel 5 and Solaris 10. This gives very clear diagnostics which helps in identifying root cause and quick defect fixes.
Website Link: Helix QAC
#23) Goanna
A security static analysis tool for C/C++ and allows integration with Microsoft Visual Studio, Eclipse, Texas Instruments Code Composer and many more IDE’s.This can be run like a compiler and hence allows analyzing file level details in addition to whole projects. Also, has excellent error reporting feature.
Website Link: Goanna
#24) Polyspace
Polyspace bug finder helps in finding defects for C/C++; this is integrated with Eclipse and also is compliant with coding rule standards like MISRA C, MISRA C++, and JSF++.
Website Link: Polyspace
#25) Sourcemeter
A tool which helps in analyzing C/C++, Java, C#, RPG and Python codes. Another good thing about this tool is it allows integration with free static checker tools like cppcheck, PMD, FindBugs. Basic Version of this tool is free but it comes with fewer features. Based on the need, you can decide whether the free version satisfies the requirement or not.
Website Link: Sourcemeter
#26) ConQAT
An excellent tool which can be used for clone detection supports multiple languages, allows integration with other static analysis tools, provides dashboard which shows the details on the issues found and other quality metrics.
Website Link: ConQAT
#27) JArchitect
An excellent tool which makes analyzing Java code simple and easier supports for Code Query over LINQ, provides a number of code metrics, allows code comparison between builds and comes with a very good customizable reporting feature.
Website Link: JArchitect
#28) OCLint
A standalone tool used for analyzing C/C++ and Objective- C programs, this supports Linux and Mac OX platforms. It does everything a static analysis tool is expected to do like finding bugs, unused piece of code, redundant code, and in addition to all that, it comes with a very customizable configuration which really helps user customize as per their needs.
Website Link: OCLint
#29) Watchtower
This tool is mainly used by a security specialist who wants to perform manual code reviews, works best on the local system, but can also scan remote websites. Maintains an extensive configuration file and hence different reporting options can be configured. Creation of alternate config files helps in the execution of multiple projects simultaneously.
Website Link: Watchtower
#30) OWASP Code Crawler
A Static analysis tool for .NET and Java/J2EE code
Website Link: OWASP Code Crawler
#31) OWASP Orizon
A tool which can be used by a security specialist to perform code reviews from a security point of view. It also provides a set of API’s which can be integrated with security tools to provide code review services.
Source Code Validation
Website Link: OWASP Orizon
#32) PC-Lint and Flexe Lint
This is the best Static Analysis tool used to test C/C++ source code. PC Lint works on windows OS whereas Flexe Lint is designed to work on non-windows OS, and runs on systems that support a C compiler including UNIX.
Website Link: PC-Lint and Flexe Lint
#33) IBM Rational Software Analyzer
IBM Rational provides the user with different types of tool, one such tool is the software analyzer which can be used for static analysis of code. This tool is designed on an extensible framework and integrates well with other Rational products.
Source Code Validation Tools
Website Link: IBM Rational Software Analyzer
Other Tools
#34) Eclair
This static analysis tool is very flexible and easily configurable tool and supports almost all platforms like Windows, UNIX, Linus, Mac OS X.This tool comes with an ability to verify conformance against a number of coding standard as well as other coding standards which include proprietary and project-based standards.
Website Link: Eclair
#35) SonarQube
It is an open source web-based tool, extending its coverage to more than 20 languages, and also allows a number of plugins.
Website Link: SonarQube
#36) Rosecheckers
If you are looking for a tool to ensure the developed code is compliant with CERT coding rules, you can opt for Rosecheckers. It is available for free is SourceForge. This tool does check for C/C++ codes and sometimes finds the problem which other static analysis tools cannot find, but this cannot be considered a full-grown standalone tool due to its inability to fully test since this is only a prototype.
Website Link: Rosecheckers
#37) Frama-c
An open source tool which lets analysis of C, comes with a very flexible framework.
Website Link: Frama-c
#38) Semmle
Open source security analysis tool for Java and C codes.
Website Link: Semmle
#39) PMD
PMD is an open source code analyzer for C/C++, Java, JavaScript. This is a simple tool and can be used to find common flaws. It also detects duplicate code in java.
Website Link: PMD
#40) FindBugs
Free tool to find bugs in Java code. It supports any version of Java but requires JRE (or JDK) 1.7.0 or later to run.
Website Link: FindBugs
#41) IBM Appscan Source
This is used to identify vulnerabilities early in the SDLC phase. Also, supports mobile scanning.
Website Link: IBM Appscan Source
#42) Flawfinder
This is an open source tool mainly used to find security vulnerabilities in C/C++ program. It can be downloaded, installed and run on systems like UNIX.
Website Link: Flawfinder
#43) Splint
An open source static and security analysis tool for C programs. Comes with the very basic feature but if additional annotations are added, this can perform like any other standard tools.
Website Link: Splint
#44) Hfcca
Header Free Cyclomatic Complexity Analyser is a tool which performs analysis and doesn’t care about the C/C++ headers or Java imports. Simple to use and doesn’t require installation. This can be used for C/C++, Java and Objective C.
Website Link: Hfcca
#45) Cloc

This utility written in Perl lets the user find blank lines, comment lines, and physical lines and supports multiple languages. Overall an easy to tool with good features like providing outputs in multiple formats runs on multiple systems and comes with an easy installation pack.
Website Link: Cloc
#46) SLOCCount
Open source tool which lets user count physical source lines of code in multiple languages and on multiple platforms.
Website Link: SLOCCount
#47) JSHint
This is a free tool which supports static analysis of JavaScript.
Website Link: JSHint
Conclusion
Above is a summary of some of the selective best Static Code Analysis Tools. Since covering all the available tools in one article isn’t possible, now I am letting the ball go in your court, feel free to bring up any tool you think is a good one for Static Analysis.